create app password office 365 powershell
Go to Users Active users. This is a strong password that you can use for an app that doesnt support MFA.
Getting Started With The Office 365 Cli The Lazy Administrator
The solve this problem you can create an App Password in Office 365.

. In the left navigation pane click Azure Active Directory. Select the Service Settings tab. From the Security and Privacytab click the Additional security verification tab and from that click the option Create and manage app passwords.
This will authenticate you using the PnP O365 Management Shell Multi-Tenant application. The only way is via the portal. Select the Create button and give the app password a name to indicate its purpose.
To use the app password in Outlook. Randomly generate a string of eight characters. Select Additional Security Verification.
Use these commands to specify a password for a user account. Open a browser and navigate to the Azure AD Portal. In the Security navigation pane click on MFA.
I have enabled the policy and now I cant run lots of the powershell scripts linked in the same Secure Score portal as the policy recommended to enable MFA for Admins. Wait for couple of minutes for Office 365 propagation and then use the app password. Search for and select Azure Active Directory then choose Users.
You can refer to this document at the allow users to create app password section. Powershell to Generate App Passwords. Login to the Microsoft 365 Admin Center.
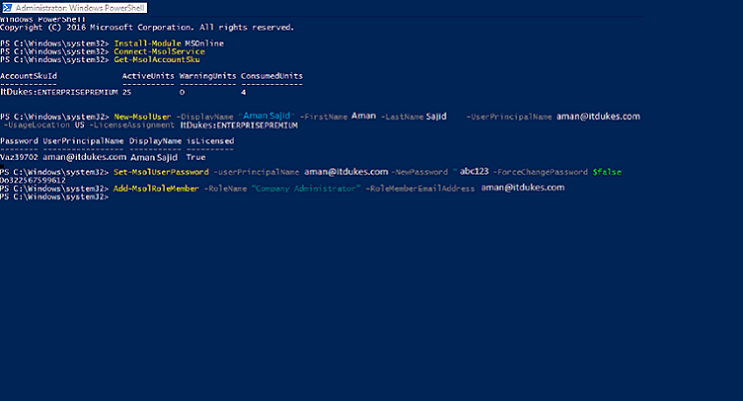
To create a user in Office 365 by using the Azure AD module I use the New-MSOlUser cmdlet. Some applications do not support MFA. If I could also make them use a complex password that would be great.
Go to the app that you want to connect to your Office 365 account. Admin could enable user to create app password but heshe cannot create app password for them. We are looking to roll out MFA for our user.
Without selecting any user click Multi-factor authentication. UserUPN newPassword Set-MsolUserPassword -UserPrincipalName userUPN -NewPasswordMissing. With my new app password I can create a new PSCredential object.
You need to be in the Authentication Administrator Azure AD role or a Global Administrator to have access to this resource. Which app in particular do you need them for afaik all first-party ones support Modern auth now. Enter any name and click on the next button.
When prompted to enter a password paste the app password in the box. And If you are using. Conditional Access MFA App Passwords and Powershell.
After clicking Next the window will display the app password and you should save it in a password credential manager as you wont be able to retrieve it. I recently took on a new customer and in part of the onboarding some passwords were changed and the link between local active directory and Office 365 with Azure AD Connect was severed. Office 365 noob here.
Click the Multi-factor authentication button while no users are selected. App passwords are auto-generated and should be created and entered once per app. There are not quite as many options but the process is very similar.
Here is the syntax for the New-MSOlUser cmdlet. Click Create and manage app password. 1 MFA is enabled on the Office 365 user account.
To generate another app password simply repeat the process. In addition for the end-user manage app passwords you could refer to here. Go to your account and select My Account Select Security privacy Click Additional security verification NOTE.
We found that for most user its complicated to generate a new Application Password. Sign in with an account that has the Global administrator or Privileged Authentication administrator role assigned. Use Windows PowerShell to force Office 365 online users to change their passwords.
3 Run the credentials script to create the username and password encrypted text files. Use the Microsoft Azure Active Directory Module for Windows PowerShell. 2 Create an App Password for the user account.
For these you will need to use what is called an App Password. To give users the ability to create app passwords admin needs to complete the following steps. Get the app password and copy it.
To create a random alphanumeric string that has two letters and two numbers use this formula. Create a new app name and click the nextbutton. CHARRANDBETWEEN6590CHARRANDBETWEEN6590RANDBETWEEN1099 Additional example is.
Allow users to create app passwords Open the Microsoft 365 admin center and go to Users Active users. Select Do not allow users to create app passwords to sign in to non-browser apps. Is there a way to generate Office 365 App Password from Powershell.
It will open a pop-up like below where you can pass user username and app password. Location securecred Get-Credential securecredUserName ConvertTo-SecureString -AsPlainText -Force ConvertFrom-SecureString set-content. In Azure Active Directorys navigation pane click on Security.
The syntax for this looks an awfully lot like the New-User cmdlet in the standard Active Directory module. This will let you access MFA settings. Select Multi-Factor Authentication from the navigation bar across the top of the Users window.
I set it back up but as we dont have Exchange it synced all of the attributes from active directory wiping out the aliases. Configuring Office 365 license app options with PowerShell Ive recently had to perform a bit of licensing management for a client because they had a set of users who have Office 365 E1 licenses assigned but the Apps configured were inconsistent across the board. Ive been struggling here a bit and there seems to be a big flaw in the Baseline Policy for MFA in the 365 portal.
First connect to your Microsoft 365 tenant. Select Create and manage app passwords last line Create a new App Password for PowerShell. I used your technique from yesterday to create a bunch of Office 365 users online and now I want to force them to change their passwords.
In the Password row of the CSV file you can use a formula such as. And you should really be avoiding the use of app passwords they are an crappy workaround which needs to die. Youll see this option only when your admin has set up multi-factor authentication for your account.
In Office 365 Admin Center go to Users Once you see all the Active Users you can simply click on Multi-factor Authentication Now youll be able to see all the users who use MFA and if they have been enforced and hence mustve created their App Passwords. Navigate to the app password tab and click the Create button. Sign in to the Azure portal.
If we can automate it via powershell and.
Powershell Support Power Platform Microsoft Docs

Resetting The Resource Mailbox Password Graham Walsh Blog

Manage Office 365 Users Passwords Using Powershell Office 365 O365info Com
Connect To Exchange Online Using Mfa Multi Factor Authentication
How To Connect To Office 365 With Powershell

Use Powershell To Log Into Office 365 Exchange
Create Office 365 User With Powershell It Dukes
How To Connect Powershell To Office 365
Cred Get Credential Without Asking For Prompts In Powershell Microsoft Tech Community

All In One Powershell Script To Perform Office 365 License Management And Reporting In A Jiffy R M365reports

3 Effective Methods To Connect To Exchange Online Powershell
How To Connect Powershell To Office 365
Office 365 Outlook For Desktop Constantly Prompts For Login Password After Enabling Mfa Two Factor Authentication How To Enable Modern Authentication For Exchange Online Jasoncoltrin Com
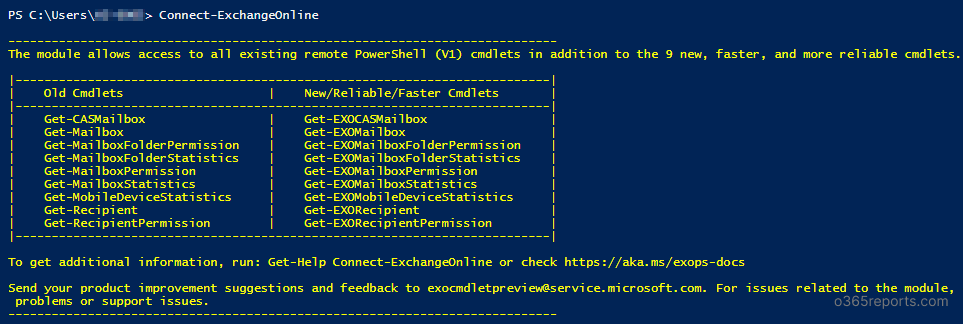
Connect To Exchange Online Powershell Without Basic Auth
Using Mfa Enabled Accounts In Powershell Scripts Octavie Van Haaften
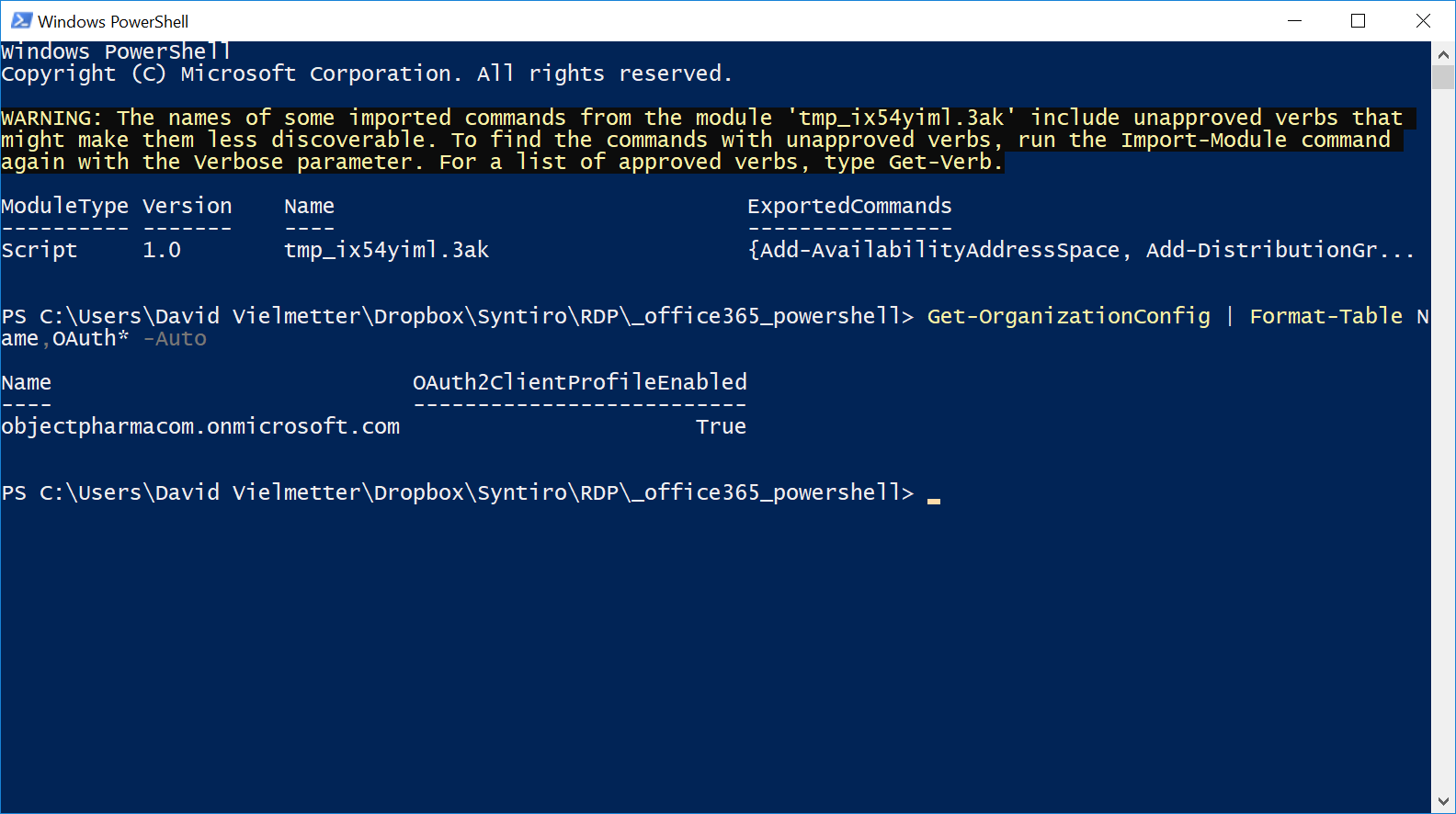
Mfa In Office 365 Finally Just Works Mostly David Vielmetter

3 Effective Methods To Connect To Exchange Online Powershell
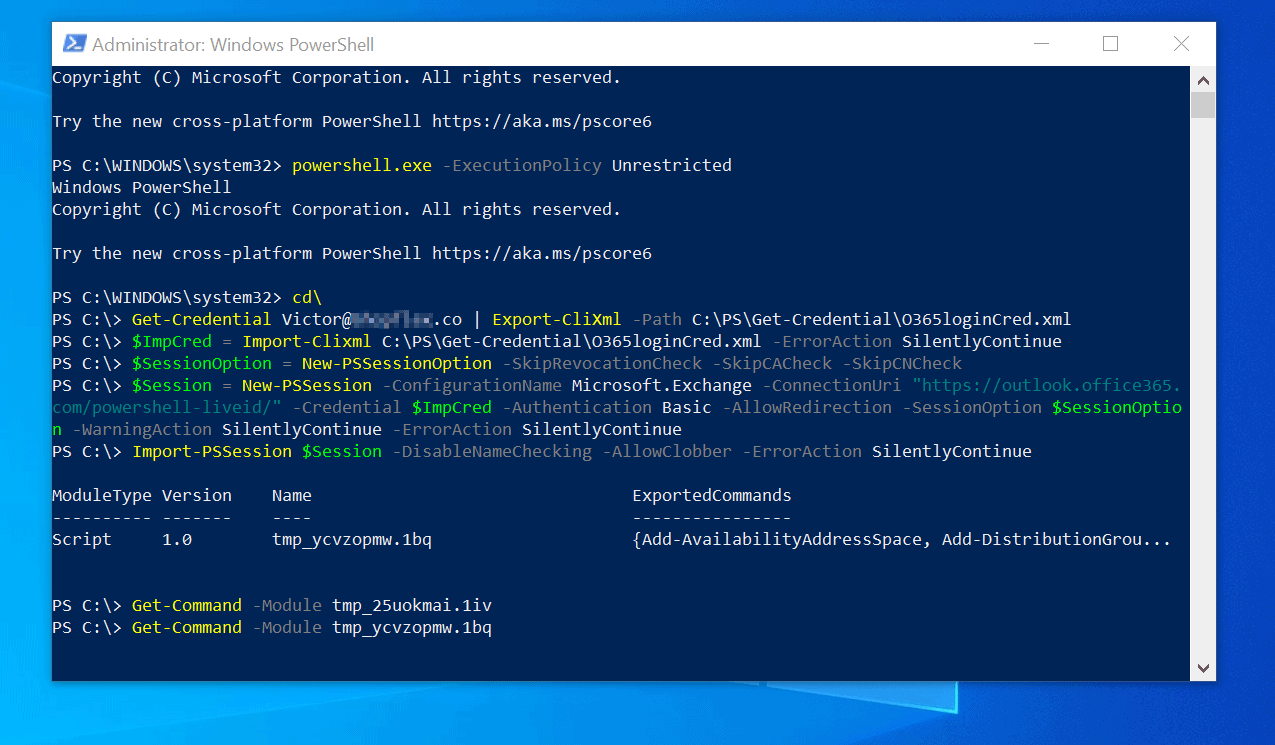
Office 365 Powershell Connect Import And Use Office 365 Ps Modules
